aarbac.NET
1.0.11.2
dotnet add package aarbac.NET --version 1.0.11.2
NuGet\Install-Package aarbac.NET -Version 1.0.11.2
<PackageReference Include="aarbac.NET" Version="1.0.11.2" />
<PackageVersion Include="aarbac.NET" Version="1.0.11.2" />
<PackageReference Include="aarbac.NET" />
paket add aarbac.NET --version 1.0.11.2
#r "nuget: aarbac.NET, 1.0.11.2"
#:package aarbac.NET@1.0.11.2
#addin nuget:?package=aarbac.NET&version=1.0.11.2
#tool nuget:?package=aarbac.NET&version=1.0.11.2
Background & Thoughts
Technology solution is vast these days, and there is always at least one solution for every technical problem. A typical application has following layers:
- Security Layer (Authentication & Authorization)
- User Interface Layer
- Business Logic Layer
- Data Access Layer
- And a RDBMS database
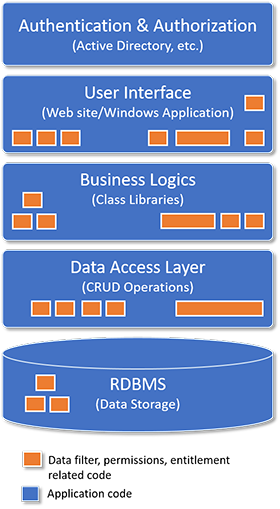
Security layer generally just performs authentication & authorization, and to facilitate roles (permissions & entitlements), developers implement various HasPermission(), IsInGroup(), etc. type methods with many ifs elses & switches, various sql queries and inject code into these layers(2, 3 & 4). Basically to enure that users with appropriate rights are performing appropriate operations. Users should see what they should see on the screens, users able to do what they are allowed to do with data.
During initial few releases, everything looks good, but messed up soon when complex business scenarios, exceptions are introduced, more ifs, switches are introduced in those layers, code quality decreases and code volume increases and makes production support & enhancements difficult. Nightmare for new team members!
What is aarbac?
aarbac is An Automated Role Based Access Control .NET framework which can override all CRUD(Create, Read Update, Delete) operations automatically based on the logged in user role. It separates out permission related code into a complete new layer and let these layers (2, 3 & 4) do their regular job & not worried about the permission at all. Additionally it also maintains user entitlements.
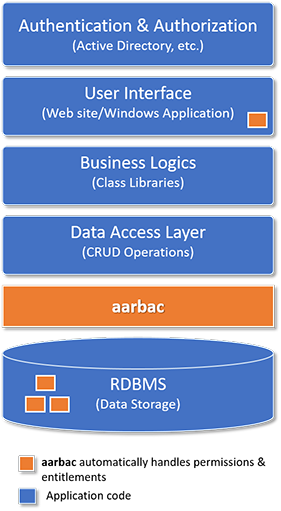
- Automated - Data Filter & Permissions are abstracted into a separate layer and all automated.
- Schema based - Data filters and permissions are based on your database schema.
- Clean Code - Clean code, less error, less testing, less maintenance.
- Encrypted - The role, entitlements & user parameters are encrypted and stored as binary in the aarbac database.
- Disable overriding for specific queries - As we do understand there will be few queries where aarbac may not able to produce automated result as desired, in those cases, just switch off aarbac.
- Comes with REST API, Utility, WinApp testbed, Sample Code.
- Pluggable.
deployed</li>
1. Automated Data Filters & Permissions (Schema Based)
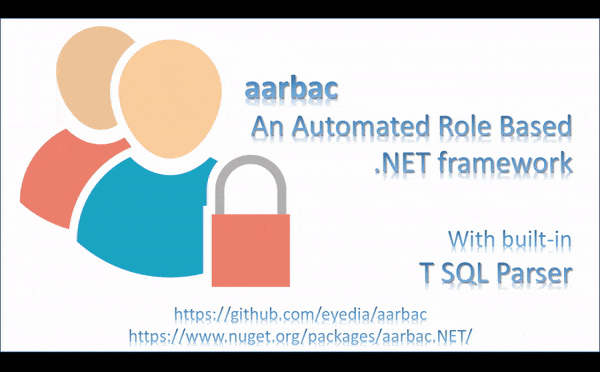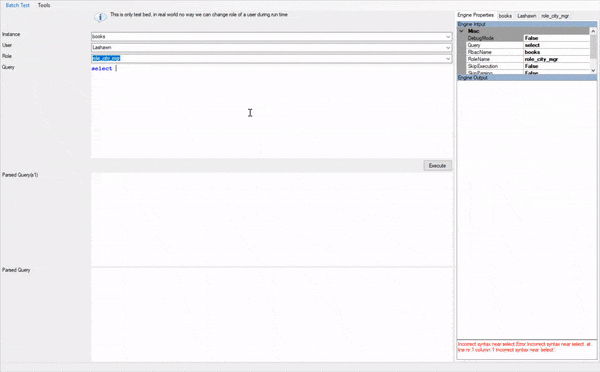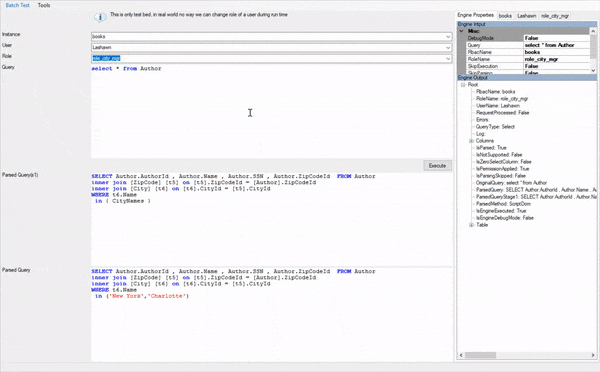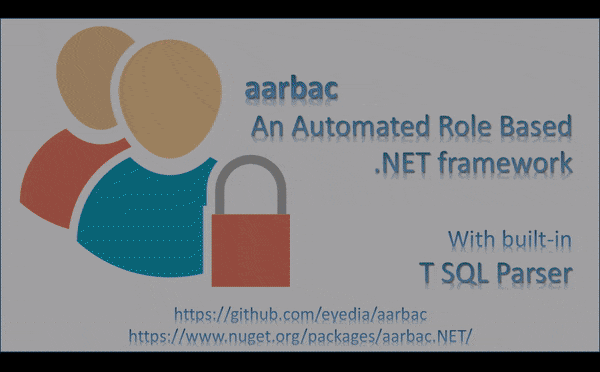
Apply row & column level permissions on your SELECT,INSERT,UPDATE & DELETE queries. For example, a read (or select) operation like the following …
select * from Author
automatically may get converted to...
SELECT Author.AuthorId, Author.Name, Author.ZipCodeId FROM Author
inner join [ZipCode] [t9] on [t9].ZipCodeId = [Author].ZipCodeId
inner join [City] [t10] on [t10].CityId = [t9].CityId WHERE t10.Name in ('New York','Charlotte')
...assuming user belongs to a role which allows him to see only 3 columns from author table and only allowed to see authors from New York and Charlotte cities.
And an update query like the following...
update Author set Name = 'Eyedia', SSN = '999-99-9999' where AuthorId = 9999
may hit exception like...
- User ‘abc’ does have permission to update table ‘Author’ but does not have permission to update column ‘SSN’
Sample Code
Select:
using (Rbac rbac = new Rbac("essie")) //<-- you should pass the logged in user name from the context
{
using (RbacSqlQueryEngine engine = new RbacSqlQueryEngine(rbac, query))
{
engine.Execute(); //<-- automatically parse and transform query based on role
if ((!engine.IsErrored) && (engine.Parser.IsParsed)
&& (engine.Parser.QueryType == RbacQueryTypes.Select))
return engine.Table; //<-- if it is select query, the table will be loaded
}
}
Inserts, updates and deletes
using (Rbac rbac = new Rbac("essie")) //<-- you should pass the logged in user name from the context
{
using (SqlQueryParser parser = new SqlQueryParser(rbac))
{
parser.Parse(query); //<-- this will throw exception if not permitted
//<-- if you are here, you are goood. Just perform basic insert/update/delete
}
}
2. Entitlements (Menu/Sub-Menu & Screen/Screen-Elements)
Every rule in aarbac has screen entitlement, you can define entitlements for your applications in following 2 categories:
1. Menus - Menu and sub menues within (linked list nodes)
2. Screens - Screen and Screen Elements (linked list nodes)
And just set visible and enabled properties on those nodes.
When user logs in, i.e. authenticated and authorized based on your authentication mechanism(for example active directory of the organization), just map user with a specific aarbac role, & each role will have entitlement. App developers need to apply the entitlement xml into the menu and screen elements.
Prerequisites:
- Microsoft SQL Server.
- .NET 4.5.2+
Release Frequency
*Every EST Sunday night *
| Product | Versions Compatible and additional computed target framework versions. |
|---|---|
| .NET Framework | net452 is compatible. net46 was computed. net461 was computed. net462 was computed. net463 was computed. net47 was computed. net471 was computed. net472 was computed. net48 was computed. net481 was computed. |
-
- CommandLineParser (>= 1.9.71)
- EntityFramework (>= 6.2.0)
- FCTB (>= 2.16.21)
- GenericParser (>= 1.1.5)
- Microsoft.SqlServer.TransactSql.ScriptDom (>= 14.0.3660.1)
- Newtonsoft.Json (>= 10.0.3)
NuGet packages
This package is not used by any NuGet packages.
GitHub repositories
This package is not used by any popular GitHub repositories.
First Release